Make it digital
Digitalize your business with internationally validated solutions designed not only for efficiency and sustainability of operational processes, but also for scalability, growth, and alignment with your business priorities. Stop adapting to software, let the software adapt to you.

Our industry-leading expertise are

DIGITAL TRANSFORMATION
Digital transformation begins with paperless operation. Automate your workflows in-house and beyond, accelerate partner-customer processes with multi-platform solutions and an intuitive user interface.
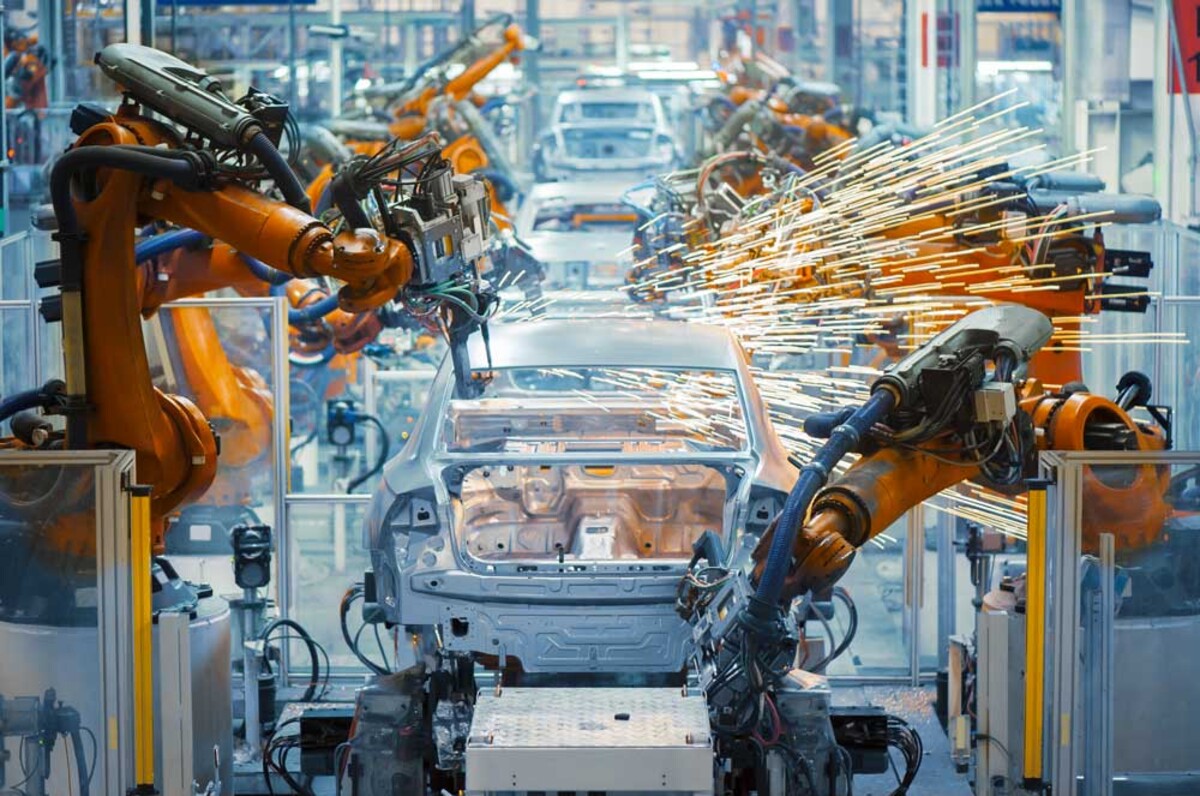
Smart industry
The Fourth Industrial Revolution is coming to your operation too. Automate the management of production-logistics processes with sophisticated systems based on Industry 4.0 principles, designed for the most demanding industrial environments and challenges.

DIGITAL PROPERTY MANAGEMENT
The most transparent way for effective economic management of residential buildings and online energy consumption monitoring. Digital management of residential and non-residential spaces is ideal for both tenants and managers.

CYBERSECURITY
Secure your corporate digital assets and IT infrastructure against advanced cyber threats. We will protect your money, data, and reputation.

customized SOFTWARE AND TAILORED SOLUTIONS
Do you have unique processes or face specific challenges? Utilize custom software engineering with personalized software considering all nuances of your business and operation.
DIGITIaliZE WITH experts
At ANASOFT, we have been dedicated to digitization for over 30 years. Our mission is to deliver information and control systems with added value, regardless of the size of your business, its focus, or your unique operational parameters. Besides design, development, and implementation of technological innovations and software consultations, we also provide management and maintenance of IT infrastructures.
Accolades

LOG-IN Logistics Innovation of the Year

PORSCHE SUPPLIER AWARD

INNOVATIVE SOLUTION AWARD

EUROPEAN BUSINESS AWARDS

VIA BONA