How to protect data from privileged users
2016-04-20
Cyber-attacks are an increasingly frequent topic of discussion these days, and part and parcel of the use of modern information technologies, which are more and more frequently confronted with sophisticated and aggressive threat of various kinds.
A wise Chinese proverb says: “He who has nothing to lose is the richest person.” Does the same apply to companies and company data? Company data stored in databases are as valuable as the “family silver” and anyone who is aware of their value knows that increased attention must be paid to them.

The 6th year of SecTec Security Day 2016, the conference oriented on IT security, which was held on April 12 at the Technopol Congress Center in Bratislava (SVK), was also dedicated to this subject. SecTec invited 18 TOP IT experts who presented the technology of respected IT security companies from around the world, including Peter Roth from ANASOFT, who demonstrated the effect of the database firewall. In his presentation he pointed out that important and confidential data can be threatened not only by external hackers, but privileged users.
The record-setting number of visitors (more than 200) was proof positive of the fact that the conference topics were interesting. As the conference partner, ANASOFT took the opportunity to conduct a survey regarding data protection in companies.
The survey results
The survey results, based on the questionnaires completed by the conference participants, revealed that awareness of IT security in companies is growing.
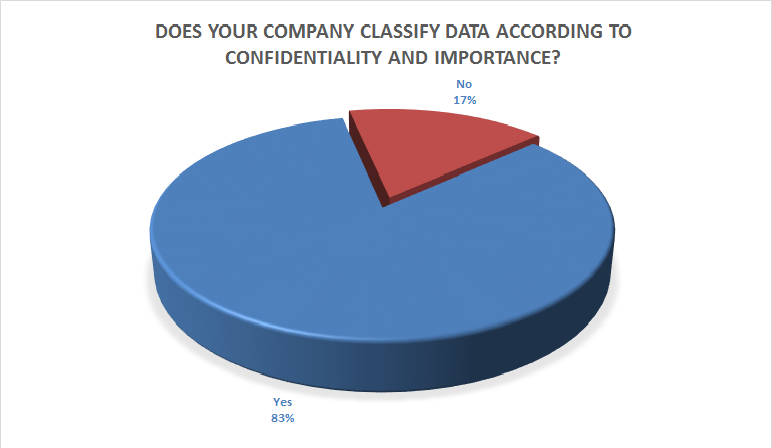
Up to 83% of the companies classify their data according to significance or confidentiality.
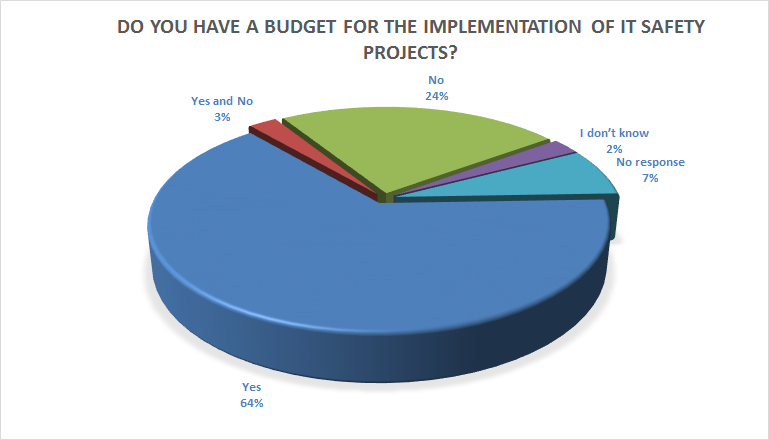
Two thirds of the respondents stated that they have a budget for the implementation of IT security projects. On the other hand, up to one fourth deal with IT security within IT projects or they lack budget resources for security projects.
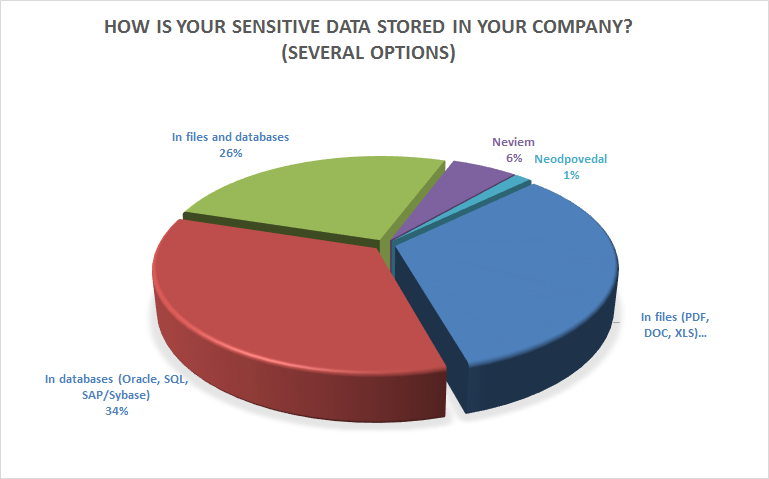
The survey results showed that almost 80% of the companies are aware of the risk arising from privileged users and they try to reduce this risk by managing access to databases or the network approximately in the same ratio. The survey further shows that sensitive data are divided approximately in the same ratio between structured data (databases) unstructured data (files) and a combination of the two.
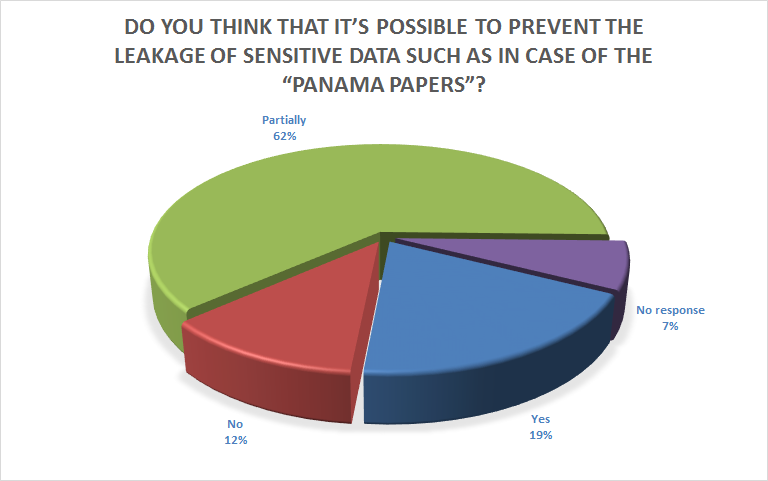
The recent leakage of sensitive data known as the Panama Papers was another area addressed by the survey. Almost two thirds of the respondents thought that it could have been possible to prevent this leakage at least partially, and one fifth felt that it could have been prevented altogether.
This result indicates that the vast majority of respondents are aware of the benefits of properly functioning IT security.
Security cannot be complete without monitoring, either independent monitoring of access to data in databases at the network level or directly through SW agents in databases, or through a solution which enables the possibility of the real-time blocking of suspicious transactions and attacks on databases to the monitoring and auditing of access to data in databases.
The monitoring of activities in databases enables compliance with the requirements of strict legislative norms and regulatory standards for data protection (PCI DSS, SOX, ISO-27001, HIPAA etc.) in cases of security audits.
Solution
We recommend IMPERVA SecureSphere Database Activity Monitoring or IMPERVA SecureSphere Database Firewall, which ensures:
- Auditing of all access to sensitive data (Regulatory Compliance)
- Warnings and/or blocking of attacks on databases, unauthorized activities
- Monitoring of privileged users – DB Admins, root, system admin
- Detection and virtual patching of database vulnerability – so called Virtual patching
- Identification of inadequate user rights, inactive users and supervision of a comprehensive cycle of user’s rights
- Acceleration of the reaction time to incidents and forensic investigation







